25. Apr 2022
My OSCP Journey
As someone who has now successfully completed the “AD” OSCP exam, I would like to share my experience in hopes to help others who are just starting out. This is gonna be part guide, part review, and part rant of my time during the PWK/PEN-200 course and the OSCP exam. And it’s gonna be a long one. I mostly wrote this to reflect on the last few months and hundreds of spent dollars. This post is gonna contain only my opinion based on my experience and is not guaranteed to get you thru the exam.
My Level at the Beginning #
For comparison I want to give you my level/experience before I started. I’ve been working in IT as a Sysadmin for some time and thus know my way around networks, computers, and servers quite well. In my private life, I balance Windows and Linux while during work I mostly come across Microsoft products. PowerShell is probably the only language that I can script in pretty fluently. I’ve been following IT Security since 2014/15 and always tried tools and new exploits against myself. Even if in the early days I didn’t really know what I was doing.
The Course Material #
All of the above is the reason that I didn’t enjoy the PEN-200 as much. Much of the course material is low-level stuff that in my opinion you should already know before trying to enter for PEN-200. I am not saying that it is bad and that I did not learn anything. If you are a total newbie it’s great. But for me, the PEN-200 contained a lot of boring topics and I think you will probably learn more on other learning platforms. I submitted the lab report but without any exercises just the required boxes.
Training Outside of PEN-200 #
I can only assume that but in my opinion, most people won’t succeed at the exam by just looking at the PWK/PEN-200 Material. Some stuff is a bit outdated and the best tools are not covered. I was however too late and not able to look at the new “Topic Exercises”. On paper, they seem a good idea. The person that told me about the OSCP exam told me right away to look at HackTheBox↗ and TryHackMe↗ and I did just that. My first six months were mostly TryHackMe (THM) or HackTheBox (HTB) based on TJNulls NetSetFocus Trophy Room↗ sheet.
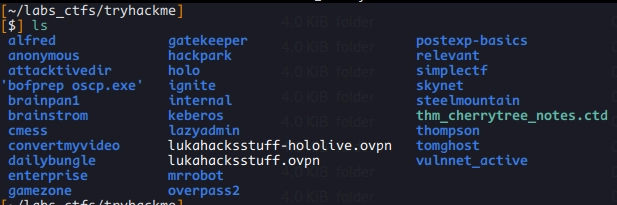
TryHackMe #
In my opinion, THM is the best platform to get started if you are a total beginner or a tech guy but a security newbie. I’ve done the “Offensive Pentesting”, “CompTIA Pentest+” and “Cyber Defense” Path (in that order). Here is a screenshot of all the rooms I did:
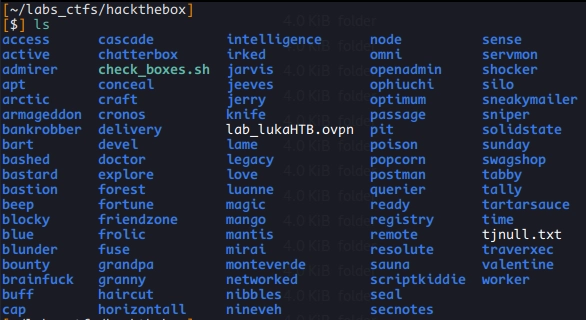
HackTheBox #
HTB is where I learned the most. Mainly thanks to this guy called IppSec↗. I think for every box on HTB he has a great video covering all the steps and often bonus stuff like other techniques or cool tools. The reason I did so much on HTB is TJNulls List↗. I was told that this is a very good list to get you prepared for OSCP. So I did just that, box after box and always randomizing my next box with a tiny script. I looked up multiple write-ups when a box was done and always watched IppSecs video if there was one. The only bad thing about HTB is that the boxes are shared. This can sometimes be really annoying. Here is a screenshot of all the boxes that I completed:
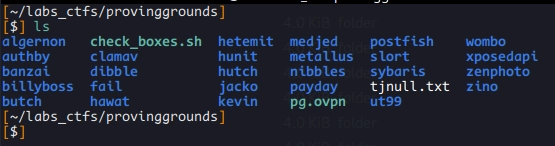
Proving Grounds #
OffSecs own CTF Platform. It’s not bad, it’s actually quite good. But HackTheBox is just better. I mainly used Proving Grounds↗ in the weeks between my exam attempts. Also, note that not many write-ups of boxes exist outside the ones provided by OffSec. The platform isn’t that old yet so maybe that will change in the future. The thing that kind off sucks is the difficulty rating. It’s good that there is a rating by OffSec and one by the community. Some boxes are labeled with “10 Points, Linux, Easy”. But when you hover over the box the community rating shows “Very Hard”. Like how can it be that there is such a wide gap? Here are the boxes that I did:
TheCyberMentor Privesc #
I did the courses on Udemy. Now they are available on his own site. If the courses are still the same as on Udemy, they are a must. I’d say that 80% of my privesc notes are from those two courses. Some methods from those courses were never needed, not on a single box. It’s still good to have seen them at least once. He also has free videos on his Channel↗.
Windows Privesc↗
Linux Privesc↗
Hot new Tips and Tricks #
Try to avoid r/OSCP #
That’s a hard one to read at first. Only visit community sites like the subreddit or the discord if you have thick skin. The problem is that most posts that I’ve seen on the subreddit are “easy, first try pass” to “failed X times” to “holy shit not doable”. Especially about the somewhat new Active Directory part. If you feel like you can handle such posts go ahead. But if you are the type of person that gets more stressed when others tell you about the exam then just ignore such places. You can get your information elsewhere.
If you are stuck look at the solution #
I’ve had multiple boxes, where I could not advance or even get a foothold. The max time I’ve set myself to advance was two hours. If I could not get any further within two hours (Identify Weakness, Foothold, Shell, Flag 1, Identify Privesc, Privesc, Flag 2) I would look at the write-up. Why? You will encounter software or techniques that you have never heard of and that’s totally okay. It’s totally okay since you are here to learn! But you need to try at least a bit before getting help. OffSecs TryHarder mindset should not be ignored. Also, I don’t have infinite time.
Do NOT upgrade your Kali Linux VM #
Oh my god. I can’t believe that I’ve never read this anywhere. If you install Kali Linux inside your OSCP VM do not upgrade it afterwards. Even after two weeks, you can have hundreds of out-to-date packages because Kali is huge. Just ignore them and only upgrade the essential stuff. (Browser, Note app, Burp, exploit-db) After my passed exam I took a snapshot and upgraded about 1500 packages. So much stuff can break by just apt update && apt upgrade -y. (Looking at you, impacket). Also a friendly reminder: Take regular snapshots of your VM and create cold backups.
For all things Python use venv #
It can be a pain at first but once you start working with venv, you will notice that all those Pythons scripts just work without you having to do the pip magic first. Basically, venv creates an isolated Python instance inside your current shell session. You can install age-old dependencies and requirements and just nuke them when done.
Never use the Meterpreter payload #
I always used netcat,nc, or inside msfvenom the shell_reverse_TCP payload. You will learn more if you do it the manual way. On the exam, you’re limited to one Meterpreter usage anyway. Sometimes, the Meterpreter payload is just too large anyway. To get around the “non-interactive shell” problem, I used rlwrap↗. This lets you use the arrow keys to select previous commands. For file transfers get comfortable with the Python http server module and the impacket-smbshare.
Stay up to date on exploits & techniques #
On most exam machines that I had, no kernel or RCE exploit that I had to use was older than a couple of months! Stay informed on stuff that happens in this fast-moving world. As soon as a new PoC hits GitHub, go ahead and download it. At least try to understand how it works. I am not an exploit expert but just by reading code comments you can try to squeeze some information out of the exploit. If you have a home lab try out the exploit against yourself. Modify the exploit, if your knowledge of the language used is strong enough. The best example for this would be that some Windows kernel exploits pop open a new cmd window as SYSTEM instead of upgrading your current shell. Not much C or C++ is needed to change that. If you see a shellcode payload inside an exploit, try to change it with shellcode generated from msfvenom. Maybe the compilation fails, maybe it doesn’t. Just try it out. For a VM I can recommend Commando↗.
For my news, I’ve been using RSS for many years. Some feeds that I can recommend to stay up to date on cybersecurity things are
- r/netsec
- Krebs on Security
- Threatpost
- Twitter (CERTs, cybersecurity news sites, CVE-Databases etc.)
Twitter for me is not really a social media. I see it more like a really fast news network. Yes, you need to fact-check most of the stuff but it’s clearly a must while working in this field.
Common Tips and Tricks #
Take notes #
Please don’t underestimate this. Choose a note-taking app, document every fcking command you enter, and possibly “tag” that command in case you will ever need it again. Trust me, you will! By “Tag” I mean if you used a SQL injection command for MSSQL then “tag” that note with SQL, MSSQL, 1433, and SQLI. I started off with CherryTree↗ but after about two weeks moved on to Joplin↗. That is still the program that I use today. Joplin has some major flaws but I got used to them. Also save every URL to any article, wiki, software, or tool that you come across. You can save them inside your notes or the bookmarks in your browser of choice.
Take breaks and do not force-feed your brain #
I liked most of the schools that I had to go to during my life. The OSCP journey was just like a school for me with the bonus that I can study whenever I want. This is a major bonus compared to traditional schools. If your head is full and trust me it will you can just stop and continue when you want or just switch to another topic. Sometimes I just could not pwn the simplest boxes. I would often take a week off and come back with new energy.
Look up many different walkthroughs online #
After doing a box/machine on any platform look up other possible solutions. Maybe there was a technique or way that you didn’t catch that will help you on another box in the future. For HackTheBox machines I can recommend IppSec↗ on YouTube.
Do not copy and paste from walkthroughs #
Just at least look at the command and try to understand what it does. This also goes for the curl https://somesite.com/somescript.sh | bash stuff. Open the script first and look at what it does.
My Tools #
During this journey, I gathered some tools, commands & techniques. Some are more useful than others. I just want to go over the stuff which you might find useful.
Tools #
PEAS↗
The new gold standard when it comes to privilege escalation. Those scripts/binaries provide so much useful information that is also colored by impact level. LinPEAS for Linux can identify so many holes that it was often the only “privesc scanner” that I needed. WinPEAS for Windows can sometimes provide a bit too much information especially when it comes to services but it is also an excellent tool for Windows privesc.
rlwrap↗
This is used together with for example netcat. If you type rlwarp nc -lnvp 80, you get a standard netcat listener on port 80. But it has the added bonus that you can use your Up-Arrow and Down-Arrow to cycle between used commands. I found that really helpful.
rustscan↗
I’d call it an “addon” for nmap. It will complete a full port scan in just a few seconds. It will increase the speed of full TCP port scans by a lot since nmap will then only scan the already found open ports. It’s however not perfect. I’ll still start a “slow” nmap afterward (just in the background) to confirm everything. For example, rustscan would in more than one case not detect an MSSQL server on port 1433. It’s still a cool tool to use.
Chisel↗
You can use this tool for port forwarding or pivoting with a SOCKS proxy. On Linux, you often can use SSH for that but on Windows, you will most likely need to provide a tool like Chisel for such a task. Putty’s plink↗ would be another option. I have a separate blog post on Chisel.
pspy↗
This will list all ongoing “tasks” inside a Linux box. With this tool, you can spot a script that is running in the background with ease. The only downside: You exit pspy with CTRL+C. If you use netcat, that will kill your shell.
suid3num↗
Also an excellent tool for Linux privesc. It uses GTFOBins↗ as a source of information. If found it will even provide you with the commands needed to escalate right when executing the script.
Flameshot↗
The best screenshot tool that I know of. The best feature: You can censor the picture right after taking a screenshot, no external tools needed.
Commando↗
This is a Windows VM for team red. It’s nice to have a Windows platform to test stuff on. Also, Visual Studio will come in handy when you need to compile Windows projects.
3bowla↗
A python3 version of the AV evasion framework ebowla. I had more success with ebowla rather than Veil.
Bloodhound↗
I used it less than I hoped to. It’s a pretty strong tool. But most boxes/challenges don’t have a big AD from which Bloodhound would benefit.
Fierce↗
DNS enumeration tool which tries the basic DNS attacks on its own. It’s also handy when scanning a DNS server for additional targets / DNS names.
LFIsuite↗
Was used to scan for LFIs. Got an “auto exploit” function as well. (about 8 different command execution methods)
Report #
I used John Hammond’s↗ oscp-notetaking↗ repo with an updated Eisvogel↗ template. The base text was taken from OffSecs own template↗.
Files #
I’ve basically made two folders: zzz_lintools and zzz_wintools. Inside those folders, I’ve gathered all my tools. Here are some screenshots of the stuff I used:
| Windows | Windows |
|---|---|
 |  |
| Windows | Linux |
|---|---|
 |  |
Exploits #
Here is my collection of exploits for Windows and Linux:
| Linux | Linux | Linux cowroot |
|---|---|---|
 |  |  |
| Windows | Windows | Windows potatoes |
|---|---|---|
 |  |  |
You can easily download the repo from below and start from there. I also never deleted an exploit after I used it. (successfully or unsuccessfully)
- https://github.com/SecWiki/windows-kernel-exploits↗
- https://github.com/Al1ex/WindowsElevation↗
- https://github.com/Ascotbe/Kernelhub↗
- https://github.com/SecWiki/linux-kernel-exploits↗
Active Directory #
Check out my AD cheat sheet here. Another good one is the one by Cas van Cooten↗.
Buffer Overflow #
The buffer overflow was never a problem for me. The BOF machines both from the lab and my exams fell within 15-30min. For learning and training, I used TCMs Buffer Overflow playlist↗ as well as THMs Buffer Overflow Prep Room↗.
Aliases #
I’ve created some aliases for easy access to my files.
# starts a web server on 8081 for all windows tools
alias wintools="python3 -m http.server 8081 --directory $HOME/tools/zzz_wintools"
# starts a smb server on \\0.0.0.0\wintools\ for all windows tools
alias wintoolssmb="impacket-smbserver wintools $HOME/tools/zzz_wintools -smb2support"
# starts a web server on 8082 for all linux tools
alias lintools="python3 -m http.server 8082 --directory $HOME/tools/zzz_lintools"
# starts a webserver on port 80 in the current directory
alias websrv="python3 -m http.server 80"
# starts a smb share on \\0.0.0.0\drop\ for the current directory
alias smbdrop="impacket-smbserver drop $(pwd) -smb2support"
# for searchsploit
alias ssp="searchsploit"
Links #
Here are some sites that I used for information.
HackTricks↗
In my next yearly donation, HackTricks will get some money for basically carrying me through this journey. It’s the best “overall” information site. If you encounter new ports there will probably be some information on HackTricks on what to do with set port. It’s also deeply connected with PEAS since those scripts will provide you with links to the GitBook when executing.
PayloadsAllTheThings↗
I’d say PayloadsAllTheThings is more technical and a bit more in-depth than HackTricks. But it’s not that easy to search for stuff that you need. I will often start on HackTricks and move on to this repo.
tennc/webshell↗
The best repo for web shells.
wwwolf-php-webshell↗
By far the best PHP webshell I’ve found.
GTFOBins↗
The best site for SUID and SUDO-based privesc on Linux. Also great for “hidden” features of some built-in tools if you for example find yourself inside a restricted shell.
WADComs↗
The best site for AD movement. You can easily select what information/access you have and this site will tell you commands on how you can try to move further inside an Active Directory.
LOLBAS↗
The Windows equivalent to GTFO bins.
MSSQL cheat sheet↗
The only MSSQL cheat sheet that I needed as a beginner.
Hash cracking
Dry Exams #
To prepare I did two dry exams.
Dry Exam 1
- 10p Sense (HackTheBox)
- 20p Cronos (HackTheBox)
- 20p Chatterbox (HackTheBox)
- 25p Jeeves (HackTheBox)
- 25p BOF brainpan1 (VulnHub, Free)
Dry Exam 2
- Algernon (Proving Grounds Play)
- Authby (Proving Grounds Play)
- CalmAV (Proving Grounds Play)
- Xposedapi (Proving Grounds Play)
- BOF Buffer Overflow Prep (TryHackMe)
Exam 1 #
Start Time 18:00 / 6PM
Points: 70, failed
I don’t want to get in trouble so I am gonna be as simple as I can regarding OSCP exam stuff.
Since I needed the AD boxes to be successful I started there. After scanning all three boxes there was an obvious starting point visible. Upon inspecting that port for like one minute it was immediately clear to me what needed to be done. After about 10min I had the first flag and my foothold on the AD environment. That gave me a huge confidence boost. If you do enough prep you will encounter this vulnerability at least once. If I had to guess I’ve seen it at least three times. After that, I spent a couple of hours getting a higher-level shell on the first AD box. At one point nothing was working so I went to the BOF.
The BOF was pretty straightforward and at least for me easy. It only took me about one hour and most of that time was taking screenshots. I used the debugging box that OffSec provides if you get the BOF for the exam. Privesc on the BOF box however was killing me. I went down two rabbit holes for nothing. In the end, I was not able to privesc due to one key factor that made that box stand out. If I would have searched long enough a higher-level shell would probably have been possible but I think that I never encountered that factor on a Windows box while training.
Before going back to the AD boxes I wanted to clear one of the standalone boxes since I needed 20 more points. After scanning both I decided pretty fast to the box with a specific service being exposed rather than a web server. The box fell pretty quickly due to a public exploit that only needed slight modification. Privesc on that box was pretty straightforward since LinPEAS told me exactly what to do. But there is something really important that I’m glad I saw. The root shell you get from the privesc is not really a valid shell that OffSec wants for the screenshots. Get familiar with how to upgrade to a real shell by for example uploading nc or dropping SSH keys.
After scoring 30 points from the BOF and the other standalone box I turned back to the AD. I was really banging my head on why the privesc was not working.
Two small tips here:
- Try more than one version of exploits you find online
- Don’t execute exploits from ‘C:\Windows\Temp\yourfolder’
That was the moment the “TryHarder” mindset kicked in. Getting a higher-level shell after about 4 hours was so satisfying. But I knew that I still needed to get the two other AD boxes to pass. But the sun was rising and I took my first bigger break.
And then came my wall. I tried every AD technique I knew but could not get any further. I scored some AD credentials along the way but I could not get code execution on the second server. I probably spent about 6 hours trying everything I could get my hands on, trying everything I learned. Especially from the PWK/PEN-200 since I read that the AD part of the exam is really just the stuff from the course. But then my notes saved me. I was going thru every AD box I ever did on any platform when I came across one more thing I could try. And it fcking worked right out of the box. That was probably the most satisfying shell that I ever got back. I guess I tried harder.
The rest of the AD boxes fell pretty quickly. The next movement steps were pretty obliviously and easy to execute. At 13:00 / 1PM I submitted the DC flag. That was the moment I knew that I had my 70 points. And it felt so good!
I did not bother with the last box but I probably found the exploit technique.
All those good feelings however would not lead to a first try pass. I was so high on caffeine and adrenaline that I forgot a screenshot inside the report. Not a proof.txt or a local.txt but rather the output of a specific command which needed to be documented. However, I only learned that 9 days after submitting my exam report. More on that later.
Exam 2 #
Start Time 13:00 / 1PM
Points: 80, passed
I got the BOF a second time and immediately started with that. It again was pretty easy. The privesc was hard but not impossible. Finding the right tool for the job was harder than imagined.
The second standalone box was also pretty easy. Port scan -> finding an app that stands outs -> exploit on exploit-db -> low-level shell -> use PEAS to get hints for privesc.
After I’ve had those 40 points it was time for the AD boxes. The first one had a similar foothold to the one on my first exam. I however could not exploit the obvious exploit. The exploit was on exploit-db but only explained manually not in the form of a script. Luckily some guy wrote a Python script only about two months prior which worked on the first try! I found that pretty fast after googling the CVE-ID. With the AD foothold in place, I wanted to do what got me further on the first exam. But that would require a SYSTEM shell.
I spent about 1,5 hours inside Visual Studio on a Commando VM trying to get one exploit to compile. And it finally did. Upon getting the SYSTEM shell I noticed however that it was not actually needed. The method which got me further this time was inside the course material. The reason this method was not my first choice is simply that it never happened to me on any platform besides the PWK/PEN-200 lab. It only works if there are multiple connected boxes. Since I documented the whole exploit rewrite stuff from Visual Studio anyway I said fck it, I may as well put it in the report.
Then came the hardest part for me on my second exam. The second and third boxes were sealed off and I had to pivot. This enforced the TryHarder mindset again since this type of pivot was actually not taught directly in the course. But upon reaching the second box the third box fell within 10min and I was done with 80 points in about 8 hours.
I then chilled a bit, collected my screenshots and notes, and tried the last standalone box again. I was able to identify the foothold but was not able to exploit it since I am not the best at this style of attack. Nonetheless, I did not submit my exam earlier. I just started with the report during the normal exam time.
Five days later I got my confirmation email and was happy to finally move on to other projects.
Money #
This whole journey cost me about 1750 CHF. That includes:
- 6 months TryHackMe
- 10 months HackTheBox
- 3 months Proving Grounds Play
- 2x Udemy TCM PrivEsc course
- PEN-200 + 60 Days of Lab Access
- Second Exam Attempt
For what I learned, this is actually not really a high number. Certifications in IT usually cost way more or at least the learning part is more expensive. I don’t think that the OSCP exam is overpriced.
Dear Offsec #
I was hoping to end this on a good note. But OffSec has made me angry more than once during my journey to OSCP. As a person who thinks that people or in this instance, a company can only evolve with feedback, I want to provide OffSec with what I think was wrong on their side.
No Email about Exam Changes #
When you announced the changes regarding the new exam structure in December 2021 you just wrote a blog post. I mean come on. You could at least have sent a mail to all current students. Please don’t bring up your newsletter as an excuse. I don’t want news about new courses or offers.
I’m not really on community platforms like Discord or Reddit so I got the news about the changes by a colleague at the end of December. It did not bother me that much since Active Directory is a part of my job and I actually like the change of winds. But you have to inform your students. You can’t simply expect that all students will get that piece of information just by talking to one another.
No Access to Topic Exercises #
A few days after you announced Topic Exercises (again, I missed that since you didn’t send an email) I sent an email to your support asking why I didn’t have access to those exercises since in your announcement you wrote: “To all current PWK students”. I only had about 3 days left from the 60 days that I bought. Your support told me to buy more days to get access. Like WTF. I still had two or three days left. You can’t write “to all current PWK students” and then tell someone to buy more days because his days are about to run out.
Why Did I Fail? #
After submitting my first exam report it took you guys 24h to respond to me that I failed. That’s really fast and I am grateful for such a fast response time. It however took you 9 additional days to simply tell me why I didn’t pass. Since I had 70 points that really bugged me. The only statement that I had was “You did not meet the requirements to pass the Penetration Testing with Kali Linux exam”. Did I break a rule? Or did I make a mistake inside the report? You need to tell people that. In my understanding, I had 70 points and did not break a rule. So it had to be a mistake inside the report. I’m gonna make the mistake again since I would have not submitted the report in the first place if I knew that there was a mistake in it. You know why I failed so just tell me that inside the “You failed” email.
Outro #
Those were some stressful months. But I’m still grateful that I did all of that. I’ll never forget my first exam attempt where I had so much caffeine that I was on fire for 36hrs straight just to fall asleep on the floor afterward. The moment the TryHarder mindset kicked in and I was finally able the clear the AD challenge was such a good feeling.
I would still recommend the OSCP exam even if OffSec did some fckups and even if I don’t think the course material is that good. I will recommend it until a competitor steps up to such a hands-on experience (at that kind of a level) and until another certification is that wildly recognized/honored/required in this community or the job market.